Related Cheatsheet : Password Attacks Some great documentation about Windows credential manipulation here: credentials
Credential storage in linux & windows environment
Password encryption format in /etc/shadow
| ID | Cryptographic Hash Algorithm |
|---|---|
$1$ | MD5 |
$2a$ | Blowfish |
$5$ | SHA-256 |
$6$ | SHA-512 |
$sha1$ | SHA1crypt |
$y$ | Yescrypt |
$gy$ | Gost-yescrypt |
$7$ | Scrypt |
See also : Linux user authentification recap
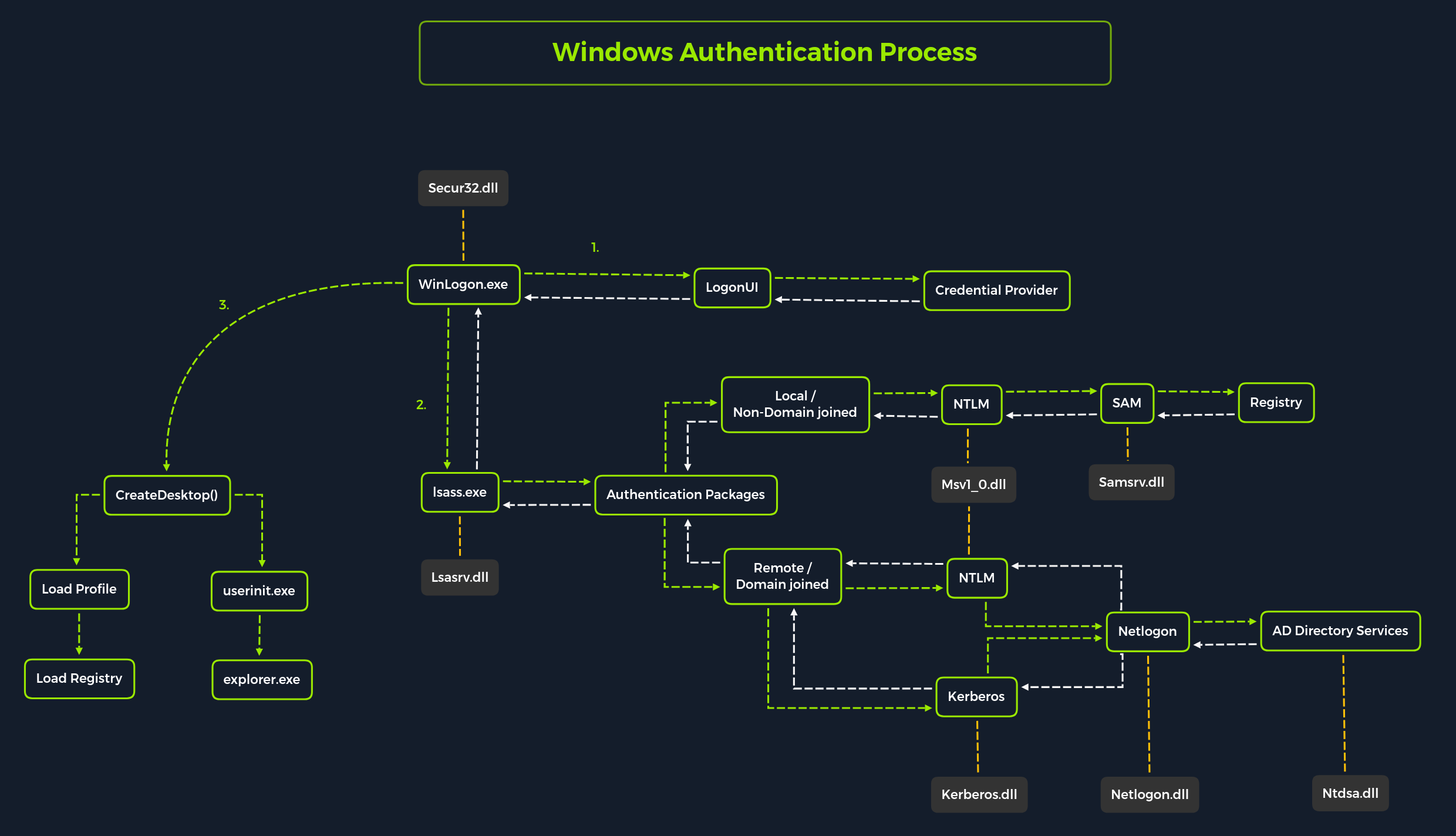
Windows Authentication
Password Attack Methods
Dictionary
Pre-gen list of known passwords, acquired from either public sources or bought to some companies / threat actors. For each password in the list, we compute its hash and compare it against the one to crack. This method is usually the one used in CTFs since all of the pentesting environment bundles rockyou, which is a very famous wordlist. This method can be also quite time consuming depending on multiple factors such has the length of the wordlist or the time needed to compute a password hash.
Brute Force
Extremely slow process used if there is no available alternatives.
This method involves computing the hash of each combination possible for a specified ruleset.
A ruleset defines what a password is made of. One example of a ruleset can be that a password is only made of alphanumeric characters with minimum 8 characters - thus matching this regex : [a-zA-Z0-9]{8,} -
Rainbow Tables
Involve the use of a pre-computed list of password hashes and their plaintext version. Also this method is really fast compared to the last two method, it’s impossible to find the plaintext version of the hash if it’s not already included in the table. Thus removing the possibility of applying mutations to the passwords we want to crack.
Windows Local Password Attack Methods
SAM
| Registry Hive | Description |
|---|---|
hklm\sam | Contains the hashes associated with local account passwords. We will need the hashes so we can crack them and get the user account passwords in cleartext. |
hklm\system | Contains the system bootkey, which is used to encrypt the SAM database. We will need the bootkey to decrypt the SAM database. |
hklm\security | Contains cached credentials for domain accounts. We may benefit from having this on a domain-joined Windows target. |
We can dump the sam database manually using reg.exe:
reg save hklm\sam C:\Windows\Tasks\sam.save
reg.exe save hklm\system C:\Windows\Tasks\system.save
reg.exe save hklm\security C:\Windows\Tasks\security.saveThen after exfiltrating the dumps, we can use impacket-secretsdump.py against the dumps:
❯ secretsdump.py -sam sam.save -security security.save -system ssytem.save LOCALOr, we can use crackmapexec to directly retrieve, decrypt and dump the SAM hash using:
❯ cme smb 192.168.1.0/24 -u UserNAme -p 'PASSWORDHERE' --samHashes cannot be dumped without the
system bootkeysince it is used to encrypt & decrypt theSAMdatabase
To crack those NT Hashes, we can put them into a file and run hashcat against it:
Info
NT Hasheshash type inhashcatis1000
❯ hashcat -m 1000 hashes.txt /usr/share/wordlists/rockyou.txtLSASS
Local Security Authority Subsystem Service (LSASS) is a process in Microsoft Windows operating systems that is responsible for enforcing the security policy on the system. It verifies users logging on to a Windows computer or server, handles password changes, and creates access tokens. It also writes to the Windows Security Log.
Attacking LSASS relies primarily on dumping the lsass.exe process in order to extract credentials that are stored in the memory of the program.
A dump of the process can be directly created from the Task Manager, by using various tools or directly from the command-line on the remote host.
Some great documentation about attacking LSASS process
NTD.dit
Ntds.dit is the main AD database file. NTDS stands for NT Directory Services. The DIT stands for Directory Information Tree. The Ntds.dit file on a particular domain controller contains all naming contexts hosted by that domain controller, including the Configuration and Schema naming contexts. A Global Catalog server stores the partial naming context replicas in the Ntds.dit right along with the full Domain naming context for its domain. One a Windows system is joined to a domain, it will no longer default to referencing the SAM db to validate requests.
To make a copy of the NTDS.dit file, we need to be in the Administrator group, Domain Admins group or equivalent.
Multiple techniques to exfiltrate the NTDS database can be found on The Hacker Recipes here: ntds or we can directly cme to extract the contents of the NTDS.dit file. This method utilize VSS as described in the previous THR link to quickly capture and dump the contents of the db.
Tip
A new tool called
ntdissectormade by the Synacktiv team was released in September, this tool is a swiss army knife for manipulating thendts.dit. You can find more about this tool on their blog and on the tools repo.